PIPEDA/PHIPA-Compliant Security for Canadian-Based Healthcare Provider
About the Canadian-Based Healthcare Provider
An organization handling medical and highly sensitive personal records needed to keep using existing web properties, built on a self-hosted WordPress CMS platform and legacy web applications. These systems, subject to PHIPA (Ontario), and PIPEDA (Canada) regulations, had evolved over time with a mix of plugins, custom code, and varied hosting environments.
Prior to our involvement, files were uploaded to WordPress via WP Forms and stored in the Media folder on a shared hosting environment. As a result, content, application logic, and regulated data were stored on the same infrastructure, including the WordPress CMS database and local file systems.
Problem / Challenges
The organization's storage model was insecure and out of step with regulatory expectations:
- Data stored on systems never designed for PHI/PII
Medical and personal records sat in the same databases and file folders as the public website, with the CMS assuming the hosting platform itself could be trusted. - Weak, inconsistent security controls
Security depended on correctly configured servers, plugins, and manual hardening. MFA was not enforced, patches were applied inconsistently, and some encryption keys were stored alongside the data or in the application layer. - No reliable, immutable audit trail
Logs were fragmented, mutable, or incomplete, making it difficult to prove who accessed what, when, or from where; an issue for PHIPA and PIPEDA audit requirements. - Breach consequences
A compromise of any CMS instance or hosting environment could grant direct access to medical files and identifiers, triggering mandatory breach notifications, investigations, financial penalties, and regulatory oversight.
The organization required a solution that would preserve its existing CMS public-facing website while ensuring that no breach of the platform would compromise regulated data, ultimately safeguarding against severe legal and financial repercussions.
The Solution
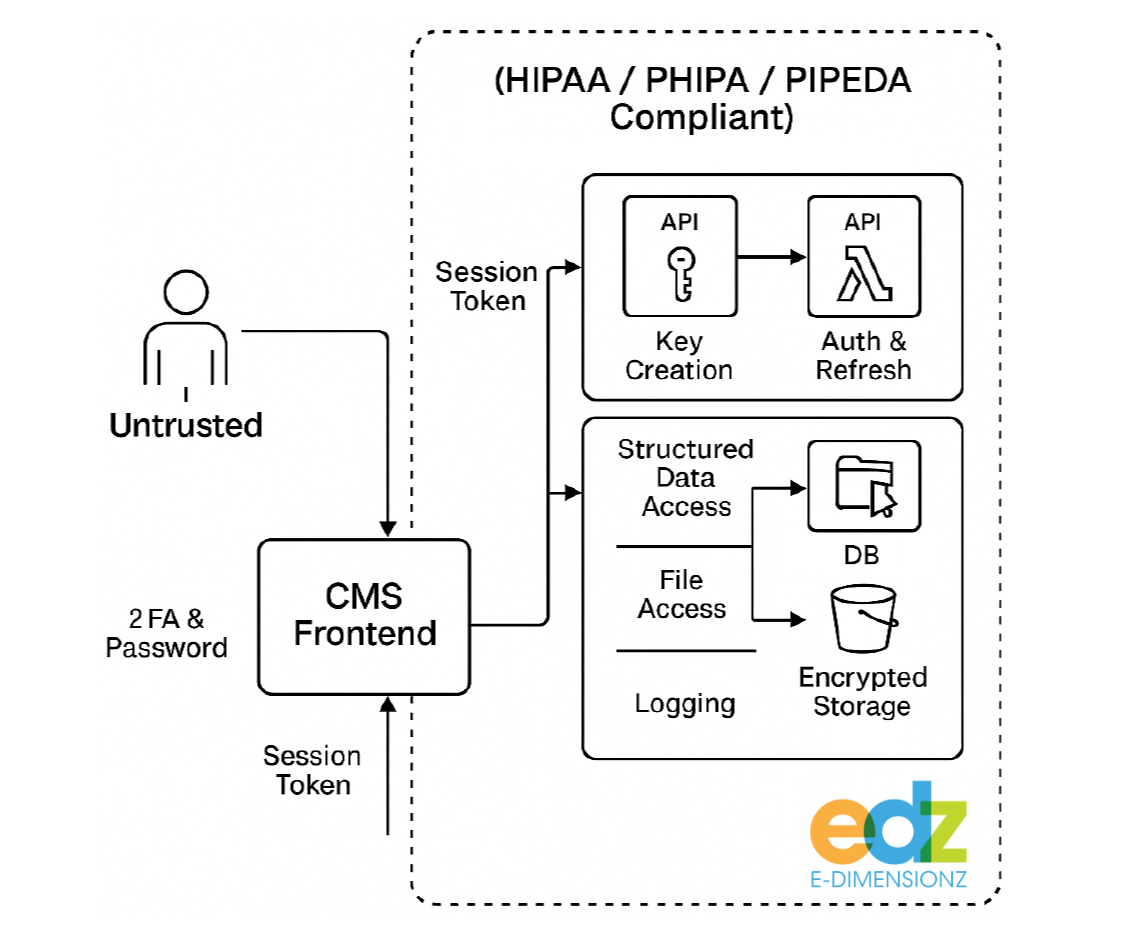
To address the organization's security risks and regulatory compliance challenges, e-dimensionz designed and implemented a robust architecture that assumes the hosting platform is insecure. By shifting critical security controls into a secured cloud environment with encrypted, region-restricted data storage, we ensured that sensitive data was fully isolated and protected, regardless of the security state of the CMS or hosting environment. The underlying cloud provider maintains independent security certifications (including SOC 1), supporting the client's compliance posture.
- The CMS becomes untrusted
- The CMS and web apps are treated purely as presentation layers.
- They never communicate directly with databases or file storage and never hold long-lived credentials, encryption keys, or privileged access.
- Identity & Session Control Moves into the Cloud
- All identity verification and session management run inside a secured cloud environment behind tightly controlled API endpoints.
- Access is granted only through short-lived session tokens tied to an authenticated identity, with multi-factor validation required at key steps. This ensures CMS-level breaches cannot be used to impersonate users or escalate privileges.
- To support this architecture, the regulated access layer was implemented using LockerRX, which provides identity-scoped access, short-lived session tokens, and audit logging without exposing sensitive data to the CMS.
- Structured Data is Fully Isolated
- Regulated records are stored in a cloud-based, identity-scoped data system that prevents enumeration, direct querying, or unauthorized access. The CMS cannot construct database queries or interact with storage directly.
- All read/write operations flow through secure, cloud-side logic that validates identity, permissions, and logs all actions.
- Files Move into Encrypted, Region-Restricted Storage
- All files previously stored in WordPress are now held in encrypted, access-controlled storage restricted to Canadian regions.
- Authorized users access files only via temporary, validated request mechanisms—never through permanent URLs or CMS-controlled processes.
- The CMS cannot browse, list, or modify stored files.
- Auditability
- Every data and file event, successful or failed, is logged in a tamper-resistant system capturing identity, intent, time, and source.
- This provides robust audit trails aligned with PHIPA and PIPEDA requirements.
In the final design, even if the CMS, its plugins, or the underlying server were compromised, access to regulated data would remain secure. Authentication, authorization, data storage, and logging all take place within a dedicated cloud security layer independent of the CMS, ensuring that the organization's web platforms function solely as frontends.
This approach allows the organization to continue using its existing infrastructure without relying on it for security, effectively isolating sensitive data from potential vulnerabilities in the platform